5 min to read
How to integrate User and Sign Risk based conditional policy in Azure AD B2C.
Microsoft introduced new feature user risk and sign-in risk based conditional policy in Azure AD B2C and secure the application. Once conditional policy is enabled in sign-in process, the organization can block the access or enable Multifactor Authentication if the user sign-in from an anonymous IP address, geographically distant locations, malware-linked IP address, suspicious browser, and shows the number of a user account is at risk and shows the risk information.
Let us see, how to integrate User and Sign in Risk-based conditional policy in Azure AD B2C sign-in.
User risk represents that given identity or account is compromised. These risks are calculated offline using Microsoft’s Azure AD threat intelligence sources. This risk is detected when user activity that is unusual for the given user with known attack patterns and user’s valid credentials have been leaked.
Sign-in risk represents that a given authentication request is not authorized by the identity owner. This risk is detected when users authenticate from Anonymous IP addresses, geographically distant locations, Malware linked IP addresses, Suspicious browsers.
License Requirement
- This feature requires an Azure AD Premium P2 license.
Steps to enable the Azure AD P2 license for your B2C tenant is given at the end of this blog.
Steps
- Enable the P2 license for Azure AD B2C Resource.
- Create a conditional access policy.
- Enable the risky based conditional access policy in user flow.
To create an Azure AD B2C tenant, follow the below docs.
Tutorial Create an Azure Active Directory B2C tenant Microsoft Docs
Create a conditional access policy
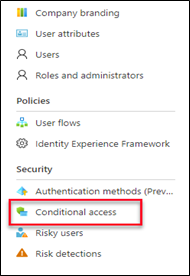
Go to Azure AD B2C resource, then click the Conditional access option under Security in the left pane.
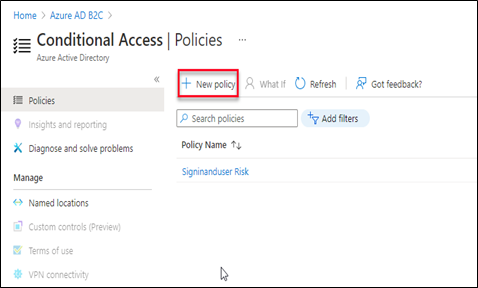
Click the New Policy button to create a new conditional access policy.
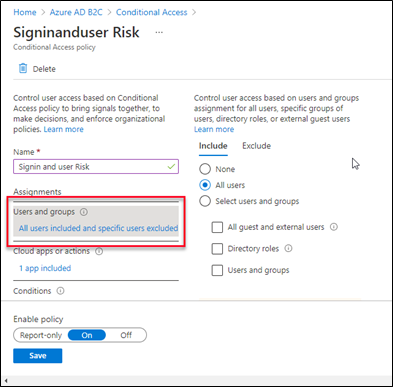
Users and groups:
A Conditional access policy allows configuring the scope to which it will be applied.This policy includes all users and exclude all admin accounts in the scope.
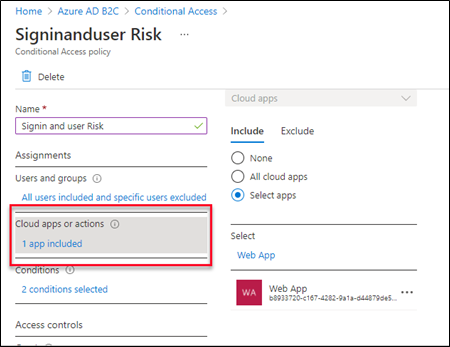
Apps:
Include all the cloud app or selected app into the policy using the option of “Cloud app or action” based on your wish.Here we included a sample web application.
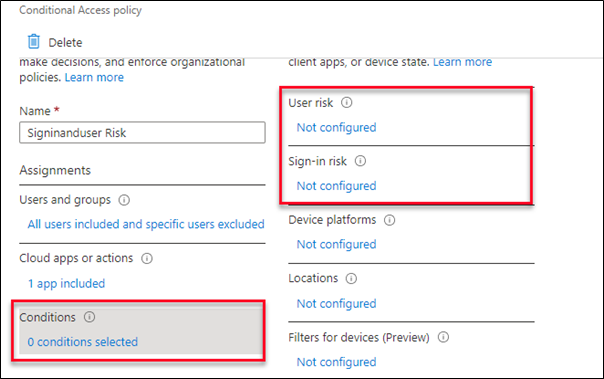
Conditions:
Condition option allows you to configure which conditions will trigger a challenge. The Identity Protection based controls are listed as user risk and sign-in risk.
User risk represents that given identity or account is compromised. These risks are calculated offline using Microsoft’s Azure AD threat intelligence sources. This risk is detected when user activity that is unusual for the given user with known attack patterns and user’s valid credentials have been leaked.
Sign-in risk represents that a given authentication request isn’t authorized by the identity owner. This risk is detected when users authenticate from Anonymous IP addresses, geographically distant locations, Malware linked IP addresses, Suspicious browsers.
Configure the user risk and sign-in risk and select the risk level based on your wish.
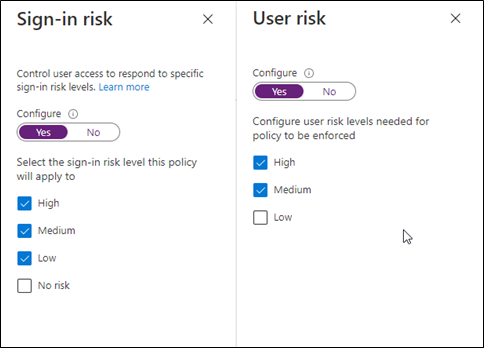
Access controls:
In Access controls, grant or block users through a particular challenge if a condition is met. Here we are using Grant access and Multifactor Authentication. If risk sign-in is detected, the conditional access policies invoke the Multifactor Authentication.
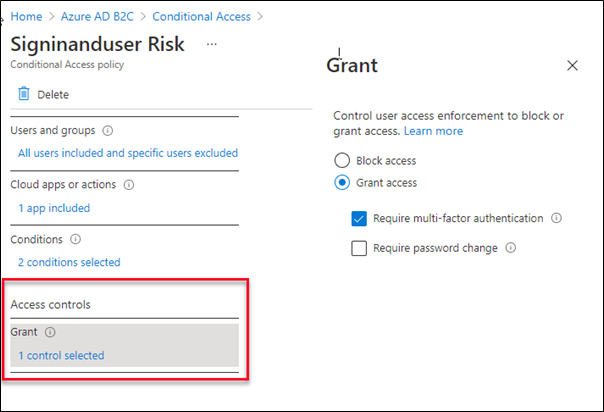
Finally, configure the all the settings and enable policy-on and save the changes.
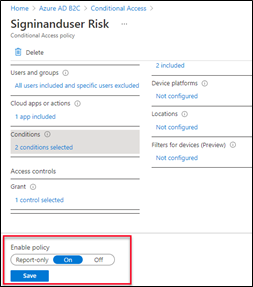
Enable the risky based conditional access policy in User Flow
Refer our previous blog to create a user flow.
https://blog.jijitechnologies.com/how-to-integrate-api-connector-in-azure-ad-b2c-user-flows
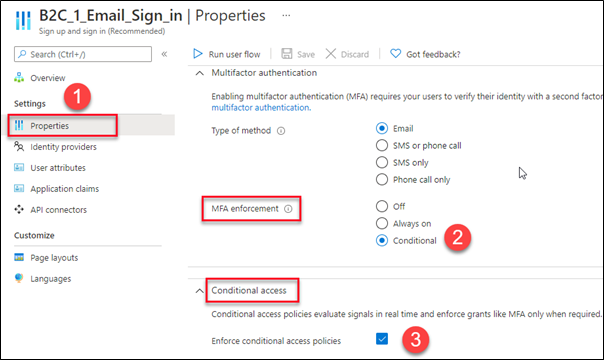
Enable Conditional access polices in User Flow
Go to user flow and select the properties option under the settings panel.
- Set MFA enforcement to conditional.
- Check the box to enforce conditional access policies.
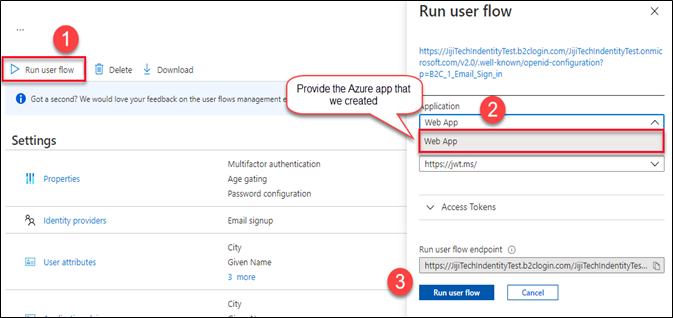
Run the user flow
Go to the user flow and click the “Run User flow “ link. It will open the run user flow popup. Provide the Azure app that we created in the previous steps. Click the user flow link or copy the run user flow endpoint for user Sign in/ Sign up process.
User experience
Sign-in from suspicious browser
Allow access with MFA
Sign in the user from the suspicious browser, conditional policies enforce the multifactor authenticator to confirm the user. Sign in with tor Browser and the sign-in process asks for verification.
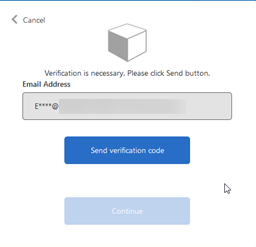
Block access
If we select a block action on Access control Option, sign in with the tor browser it will block the user access and shows the below message.
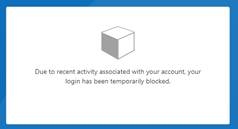
Admin experience
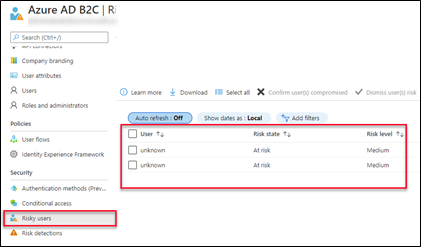
Find a user account is at risk
Here we are using a user risk policy, go to Azure AD B2C resource and the Risky user tab under the security panel shows that the user is at risk.
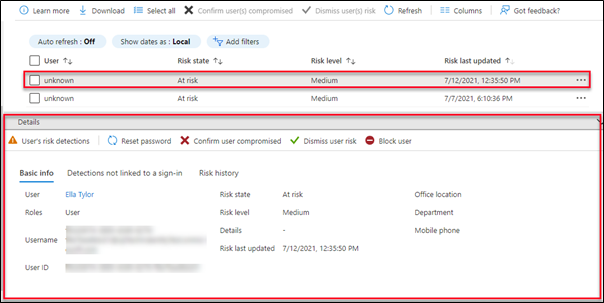
Select the user, it shows the user information and which action will be taken on risk user such as change password, dismiss user risk, block user.
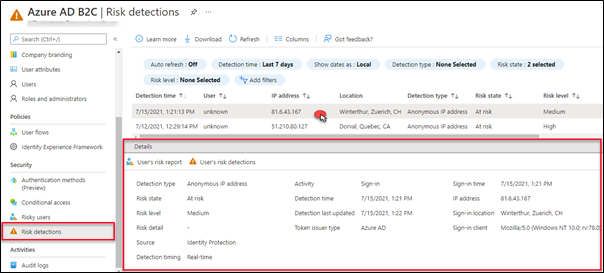
Find the risk details
To get more details about risk, go to the Risk detection tab under the security panel.
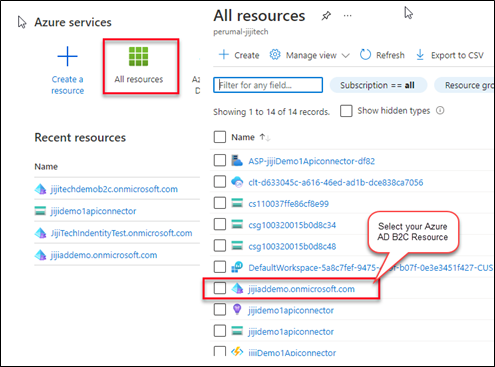
Enable the P2 license for Azure AD B2C Resource
Go to the Azure portal and select all resource tab and then click the created Azure AD B2C resource.
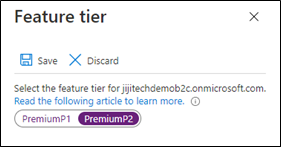
In the overview tab, the pricing tier option is shown under the Essentials plane.
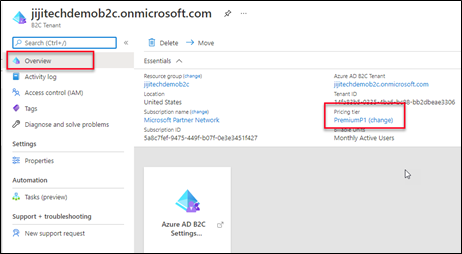
Click the link to the pricing tier, it will open the popup.
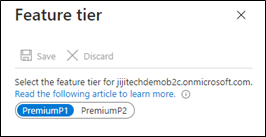
Switch the license from P1 to P2 and save the changes.