6 min to read
Microsoft Teams App Permission Policy

What is Teams App Permission Policy?
Today with the introduction of Microsoft Teams App Permission Policy, as an admin we can start provision different of apps to different teams in Microsoft Teams. Earlier, we had organisation wide settings in Office 365 Admin centre to disable the apps to your entire tenant. With Teams App Permission policy, we can define what are app users can use in user level.
Categories of Teams apps
There are three types of Teams apps is available, that is
- 1st Party App or Microsoft App (Inbuild Microsoft App like SharePoint, Planner, PowerApps, Etc…)
- Third party App (Non-Microsoft apps like Trello, Jira, Twitter, Etc… published in the store)
- Custom App or Organisational App (Custom developed app and used for internal organization)
How to Manage Teams apps in tenant level
Previously tenant admin can manage tenant level Teams apps from Admin center Services and add-ins Microsoft Teams Apps.
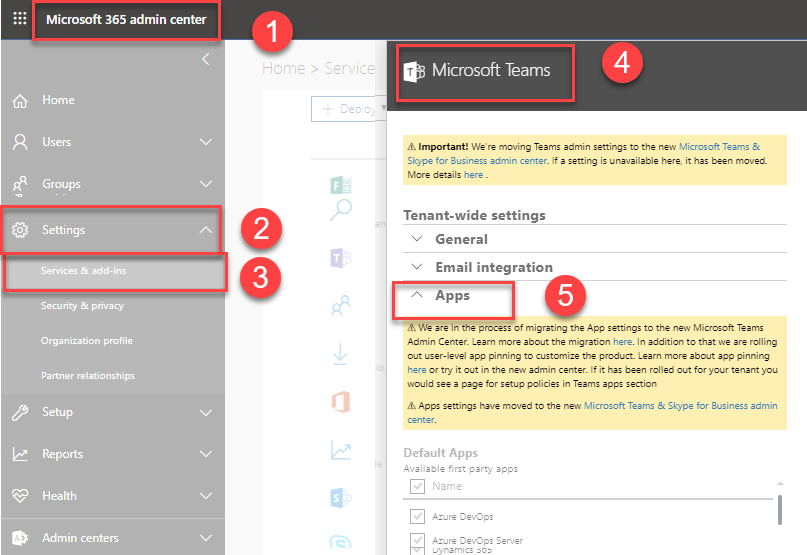
But this functionality is migrated to Microsoft Teams admin center. Microsoft Teams admin center Teams Apps Permission Policy Org-wide app settings.
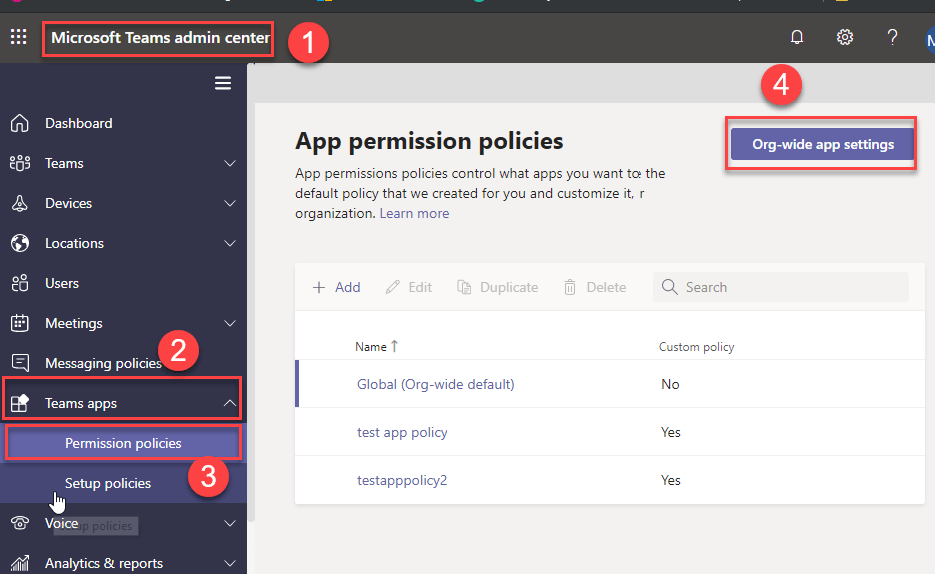
What are the features available in the Org-wide app settings?
There are three types of feature are available in the Org-wide app settings and Org-wide app settings override any other app permission policies assigned to users.
- Third Party apps
- Custom apps
- Blocked apps
Third Party apps
In the third-party apps section, we can control the following settings at the tenant level.
- Allow third party or custom apps
- Allow any new third-party apps published to the store by default
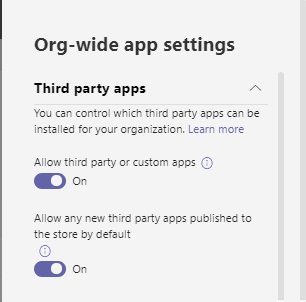
Allow third party or custom apps
Turning off this setting prevents all the users in the tenant to install the third-party apps and custom apps in teams.
Allow any new third-party apps published to the store by default
Turning off this setting prevents users from installing new third-party apps that are published to the Teams app store.
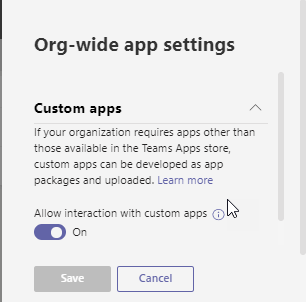
Custom apps
Custom apps section, we can control custom app upload in tenant level using Allow interaction with custom apps turn on or turn off settings.
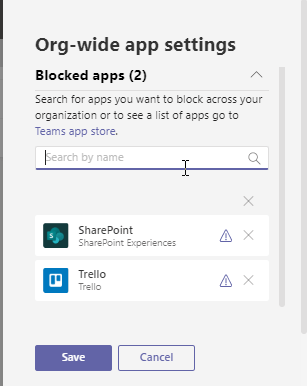
Blocked apps
Blocked apps section we can block app (Microsoft apps, Third party app) globally.
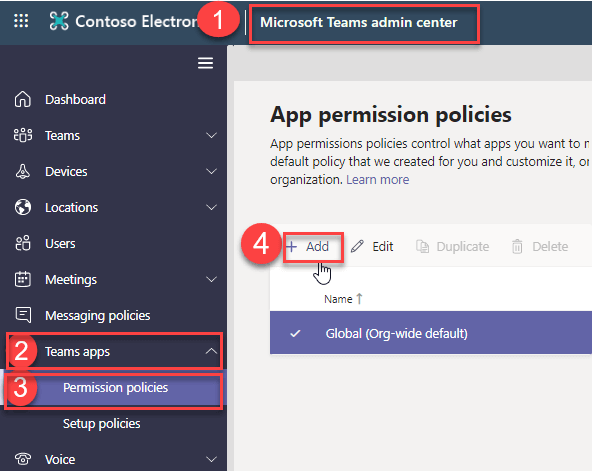
How to create Teams App Permission policy
Teams App Permission policy requires Teams Service Administrator permission to create and manage permission policy. Teams administrator can create the app setup policy from Teams Admin Center Teams apps Permission policies Add Policy.
In the Teams app permission policies have three categories.
- Microsoft App
- Third party App
- Custom App
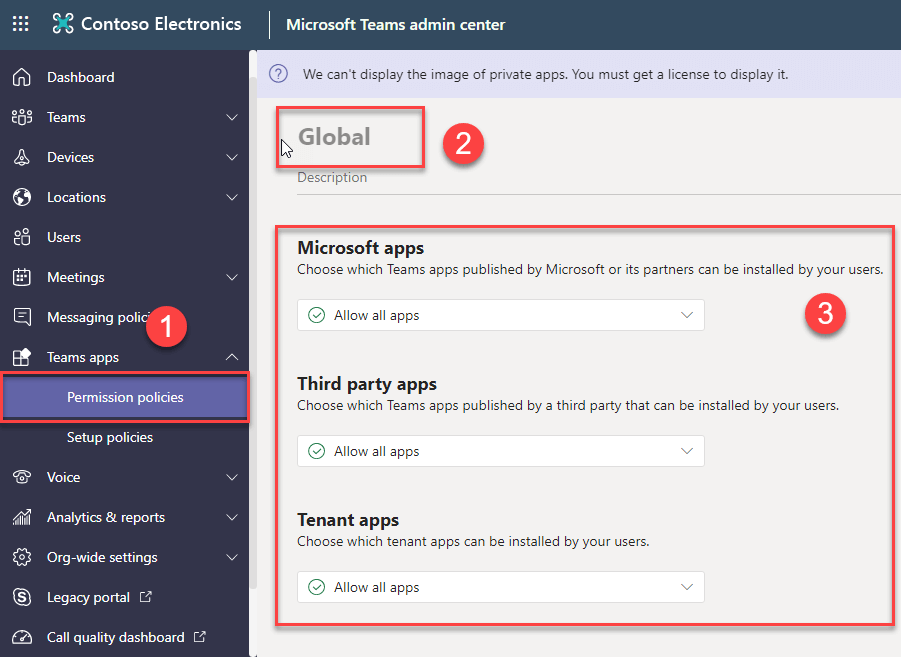
We need to define each category in the Teams custom app permission policies. In each category, we need to select any one of the options as showing below.
- Allow all apps
- Allow specific apps and block all others
- Block specific apps and allow all others
- Block all apps
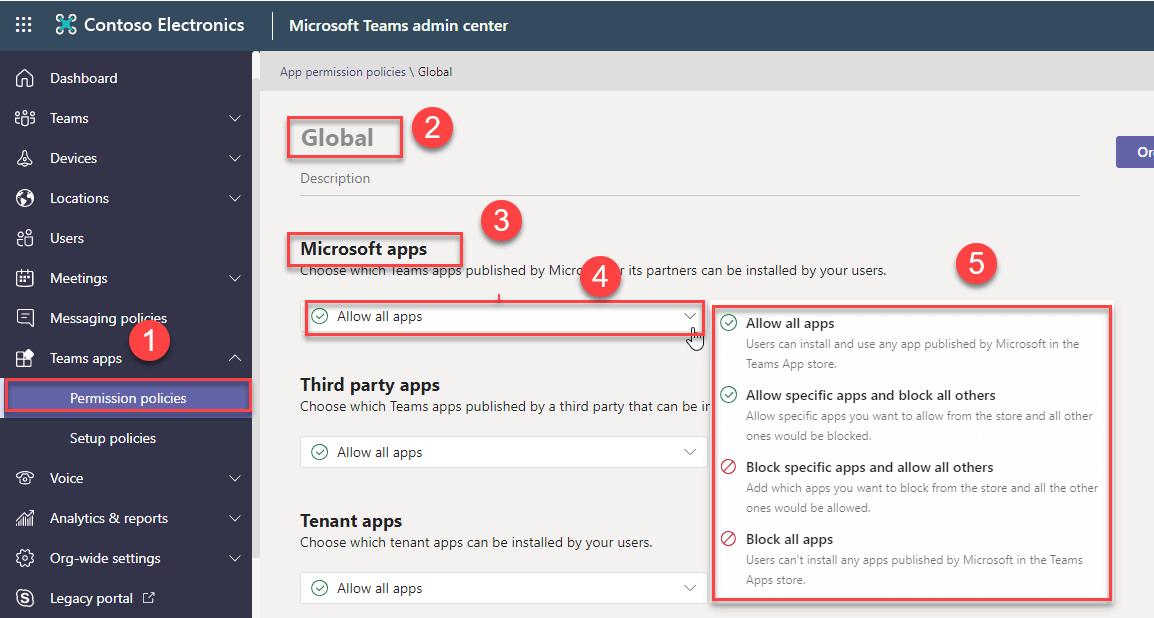
Applying setting in Microsoft apps
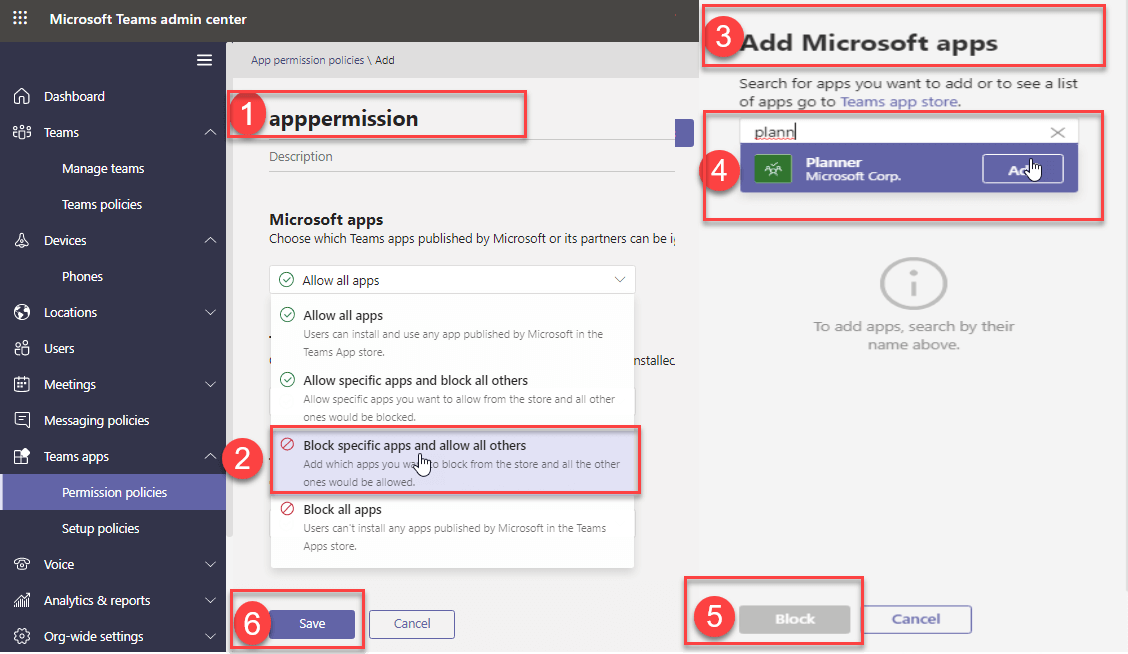
How to apply Teams app permission policy to users
Once created the Teams app permission policies from Teams admin center. We need to apply this policy to users. We can apply this policy in two ways. That is
- Apply policy from Teams admin center.
- Apply policy using Skype PowerShell module.
Apply policy from Teams admin center.
We can apply app permission policy from two ways in teams admin center. That is
- Users section
- App permission policy section
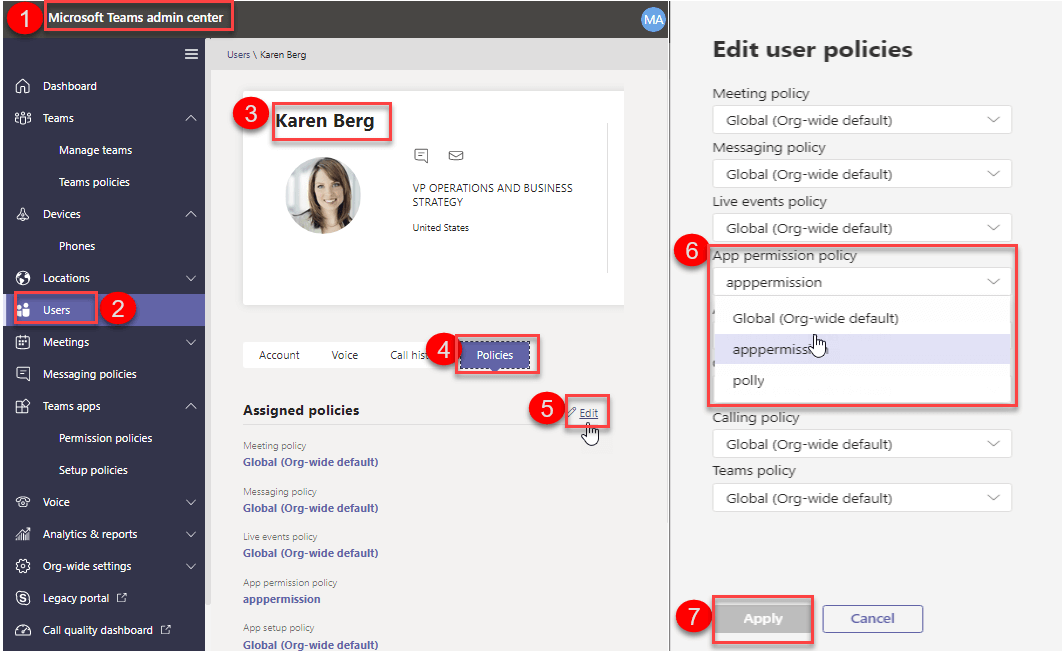
Users section
We can apply Teams apps permission policy to user from Teams admin center. Go to Teams admin center Users Select required User click Polices Click Edit Select required a policy in the App permission policy Click Save.
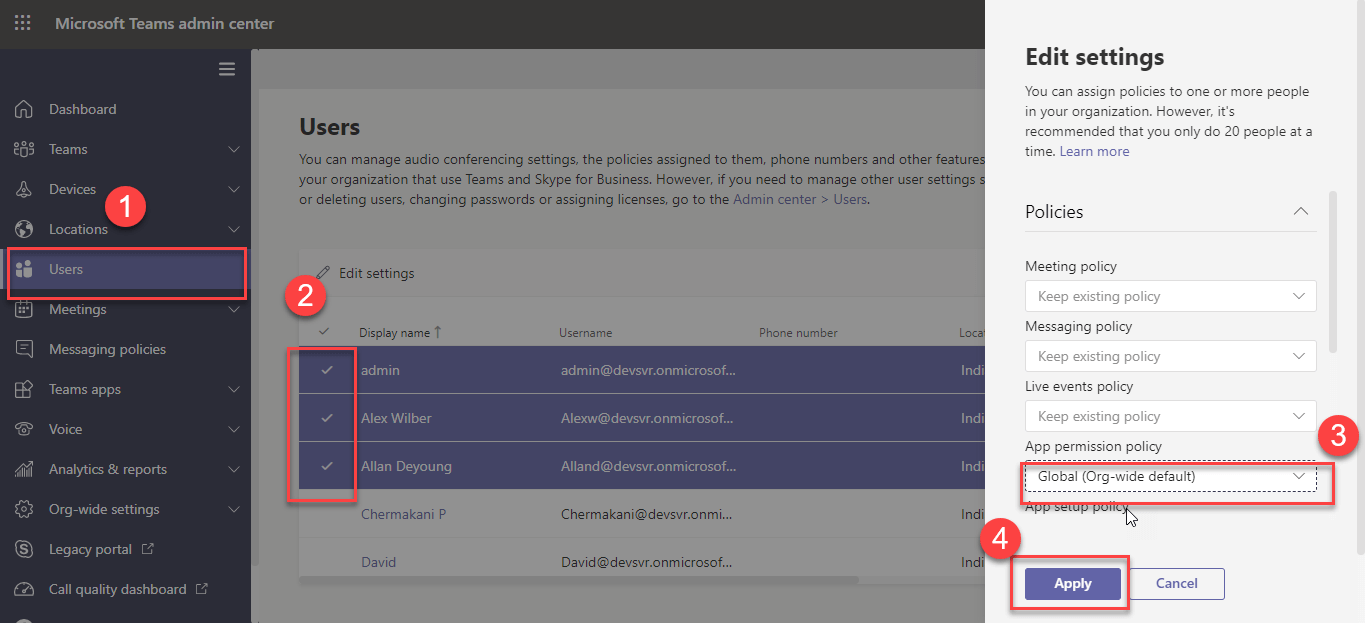
Bulk update policy
We can bulk apply Teams apps permission policy to user from Teams admin center. Go to Teams admin center Select multiple Users Edit settings Policy Select required a policy in the App permission policy Click Save.
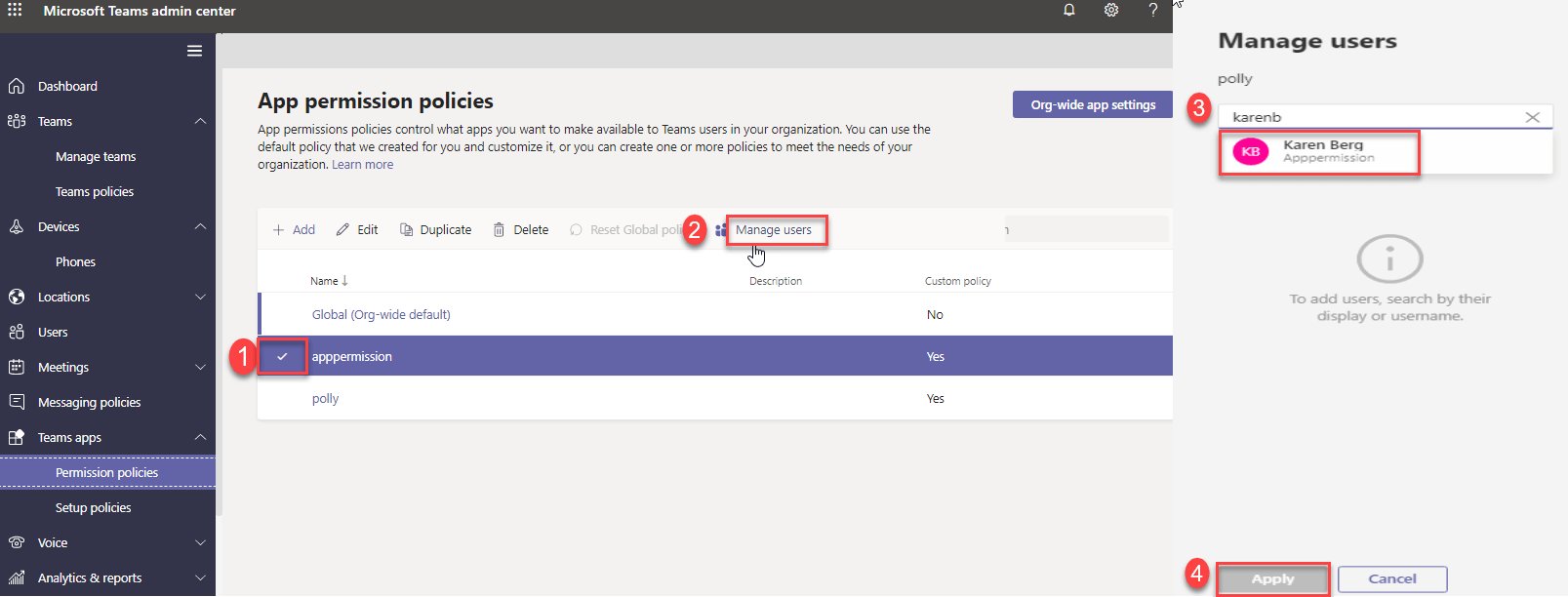
App permission policy section
We can apply Teams apps permission policy to user from App Permission policy itself using Manage Users option. Go to Teams apps Permission policies->Select required Policy Manage Users Add required Users.
Apply policy using Skype PowerShell module
We can apply the Teams app Permission policy to users using Grant- CsTeamsAppPermissionPolicy cmdlet in Skype for Business PowerShell module. You can apply this policy in two ways using PowerShell.
- Apply the policy to security group member
- Apply policy using CSV file.
Apply the policy to security group member
Using this script, we find all member in a particular security group and apply the policy to all members. This script required two modules that is Microsoft Azure Active Directory Module and Skype for Business online PowerShell module.
function Set-TeamsAppPolicy
{
param (
$GroupName,$AppPermissionPolicyName
)
process{
$cred = Get-Credential
#login into Azure Ad powershell module
Connect-MsolService -Credential $cred
#login into Skype online powershell module
$session = New-CsOnlineSession -Credential $cred
Import-PSSession $session
#Get security group information.
$group= Get-MsolGroup -SearchString $GroupName |select ObjectId,DisplayName
$members=Get-MsolGroupMember -GroupObjectId $group.ObjectId -MemberObjectTypes user -all
#Add user to App permission policy
foreach($member in $members)
{
Grant- CsTeamsAppPermissionPolicy -PolicyName $AppSetupPolicyName -Identity $member.EmailAddress
Write-Host "Policy successfully added to $($member.EmailAddress) user "
}
}
}
Set-TeamsAppPolicy -GroupName Testsecgroup -AppPermissionPolicyName "Dev team policy"
Apply policy using CSV file
Using this script, we can apply the policy to all user in the CSV file. This script only required Skype for Business online PowerShell module.
function Apply-TeamsAppPolicyUsingCSV
{
param (
$ImportPath
)
process{
$cred = Get-Credential
#login into Skype online powershell module
$session = New-CsOnlineSession -Credential $cred
Import-PSSession $session
#Get user information from csv file.
$users = Import-Csv -Path $ImportPath
#Add user to App Permission policy
foreach($user in $users)
{
Grant- CsTeamsAppPermissionPolicy -PolicyName $user.PolicyName -Identity $user.EmailAddress
Write-Host "Policy successfully added to $($user.EmailAddress) user "
}
}
}
Apply-TeamsAppPolicyUsingCSV -ImportPath c:\Userslist.csv
User Experience
Now we applied policies to users. Here, we listed down the user experience based on blocked access for the specific application.
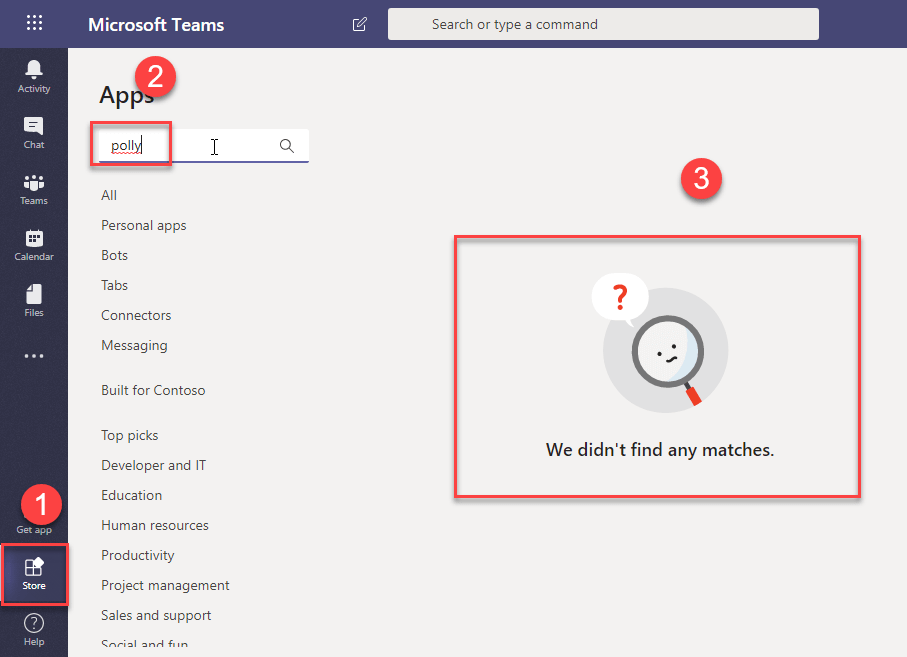
App Search option in app store
If the applied App Permission for user blocks Polly, then this app will not be listed in the App store and search in the app store.
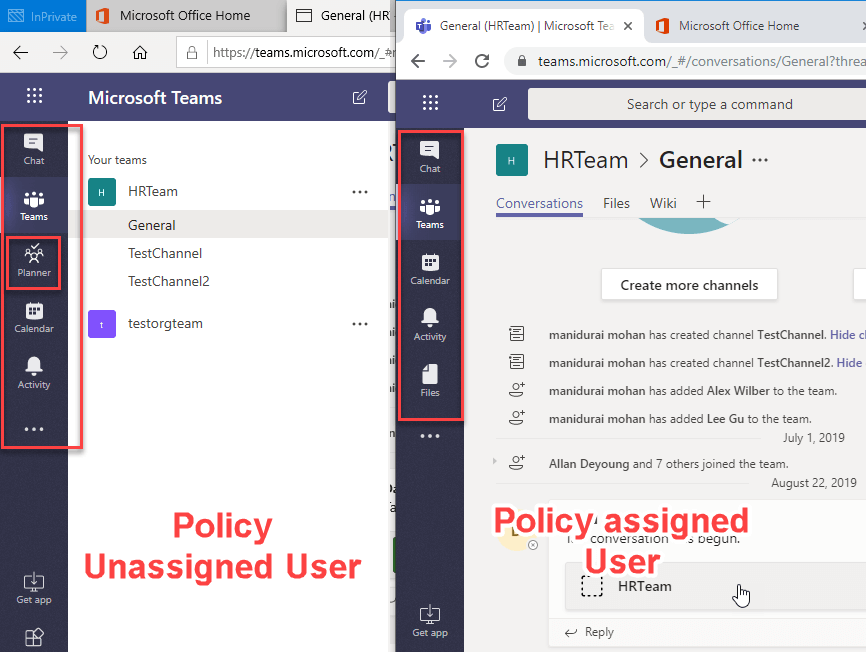
Pinned app
If the user access is blocked for Planner application and if it is pinned in the side navigation, it will be removed.
Teams Application tab
If the user access is blocked for Planner application and if it is added as tab, it will be removed from the Teams tab.
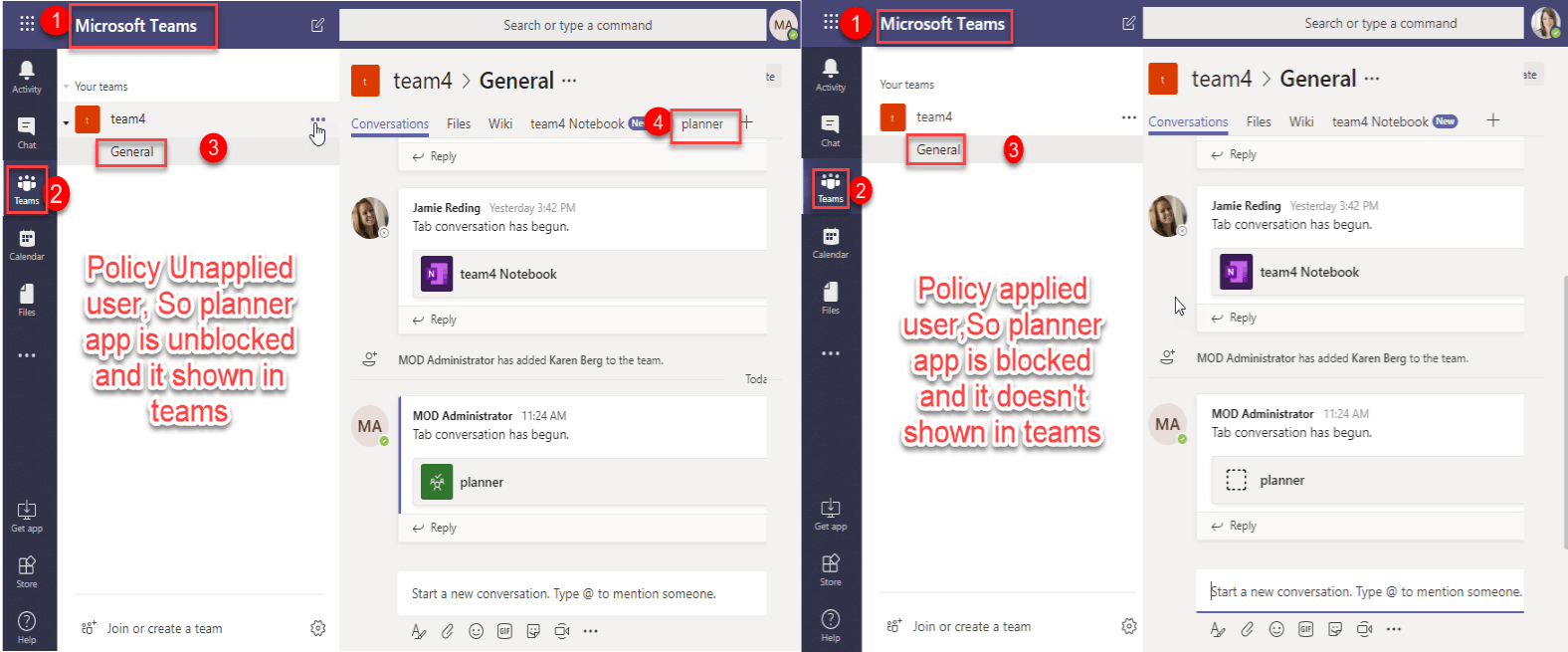
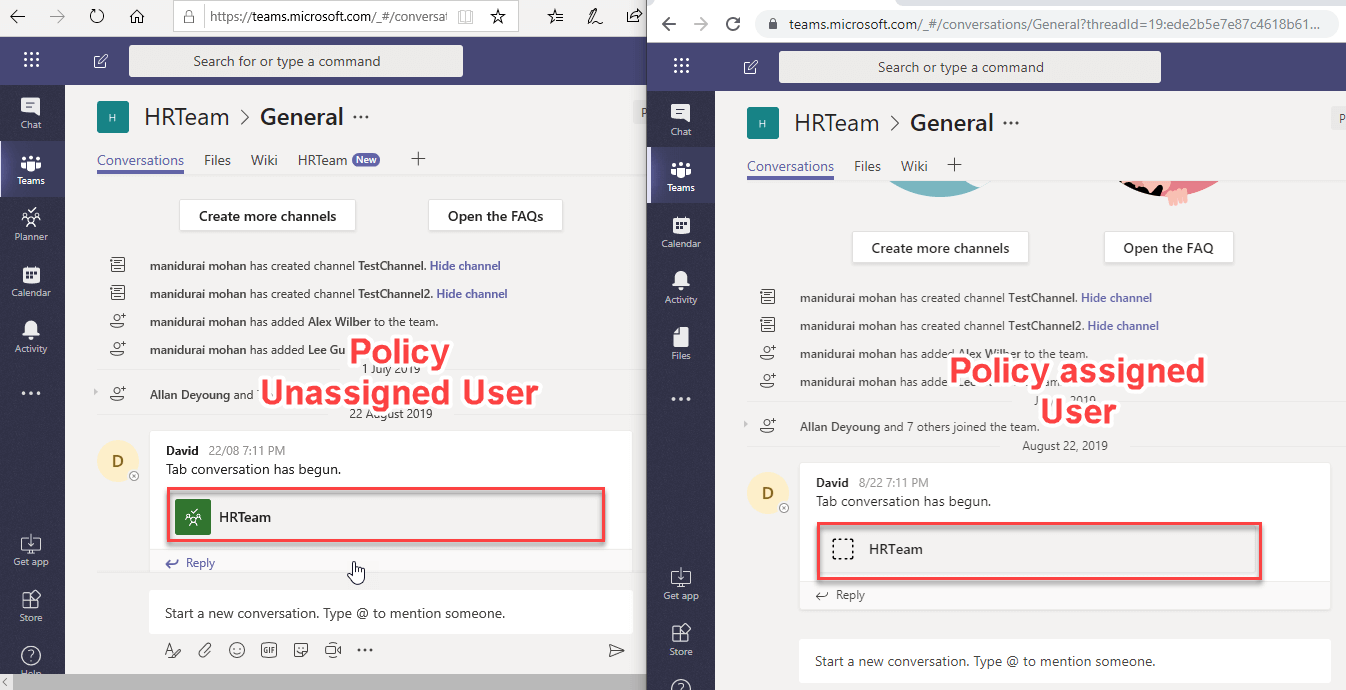
Tab app Conversation
If the user access is blocked for Planner application, that user unable to access the tab app in the Teams conversation.